Petrwrap, a new ransomware strain that uses the same SMBv1 worm as last month’s WannaCry outbreak, is crippling businesses, banks, airports, and utilities across Europe with Ukraine’s government and state-run services at the centre of the damage.
Security teams are working to beat back a new ransomware strain that is quickly spreading across Europe and beyond, there are uncomfortable questions that have to be asked: Why is a ransomware strain employing the same vulnerability WannaCry used causing so much damage? Why haven’t businesses patched their systems and improved their defences after the last month’s worldwide WannaCry wakeup call?
The initial attack vector appears to have come from an Ukrainian accounting software called MEDoc.
Once this modified version of Petya infects the network it continues spreading using
1 – Windows shares using the victims stolen credentials. This is done using a bundled Mimikatz like tool which extracts passwords from memory.
2 – By using the two SMB vulnerabilities EternalBlue (the same vulnerability as WannaCry) and EternalRomance. Patches for these two vulnerabilities have been available from Nicrosoft since March 2017.
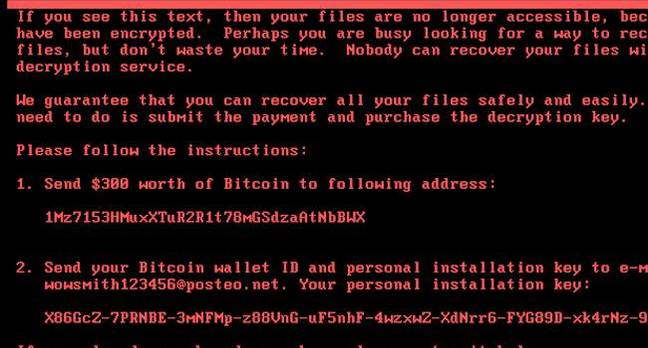
The virus encrypts the MBR on the hard drive and reboots the machine, Once rebooted it starts to encrypt your files. If you are able to stop the machine fully rebooting (pull the plug) it may be possible to recover your files using an off-line process.
Needless to say, don’t pay the ransom – there’s no way to get the necessary keys to restore your documents. It appears the malware doesn’t provide enough information to the extortionists for them to generate a correct unlock key, so it would be impossible to obtain a working decryption key from the crims. And the means to contact the miscreants after paying the money is now shut off, so you’re out of luck regardless. In addition the email address they have been using has now been disabled, so you can’t even tell them you have paid.
If you are using an up to date anti-virus (Midgard recommends Avast), you should be safe. If your PC is fully patched, you should be safe.
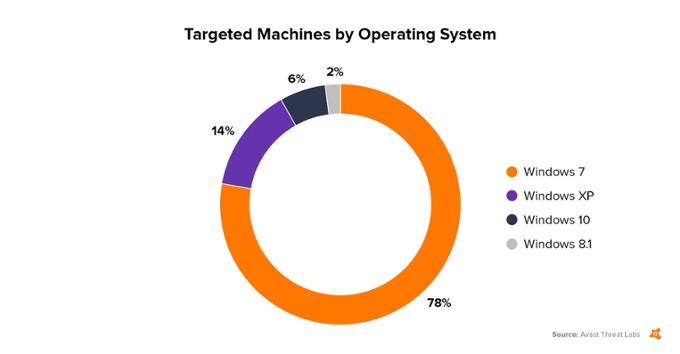 These two recent attacks have affected many businesses and organisations across the world. Midgard are pleased to confirn none of our customers have been affected by either attack.
These two recent attacks have affected many businesses and organisations across the world. Midgard are pleased to confirn none of our customers have been affected by either attack.
Contact us if you want to know how we can secure your business.